Last Thursday, investors in hedge fund Angelo Gordon received an unpleasant letter advising them that a “data security incident” had taken place due to a breach of a third-party vendor used by the fund’s external fund administrator, SEI Global Fund Services.
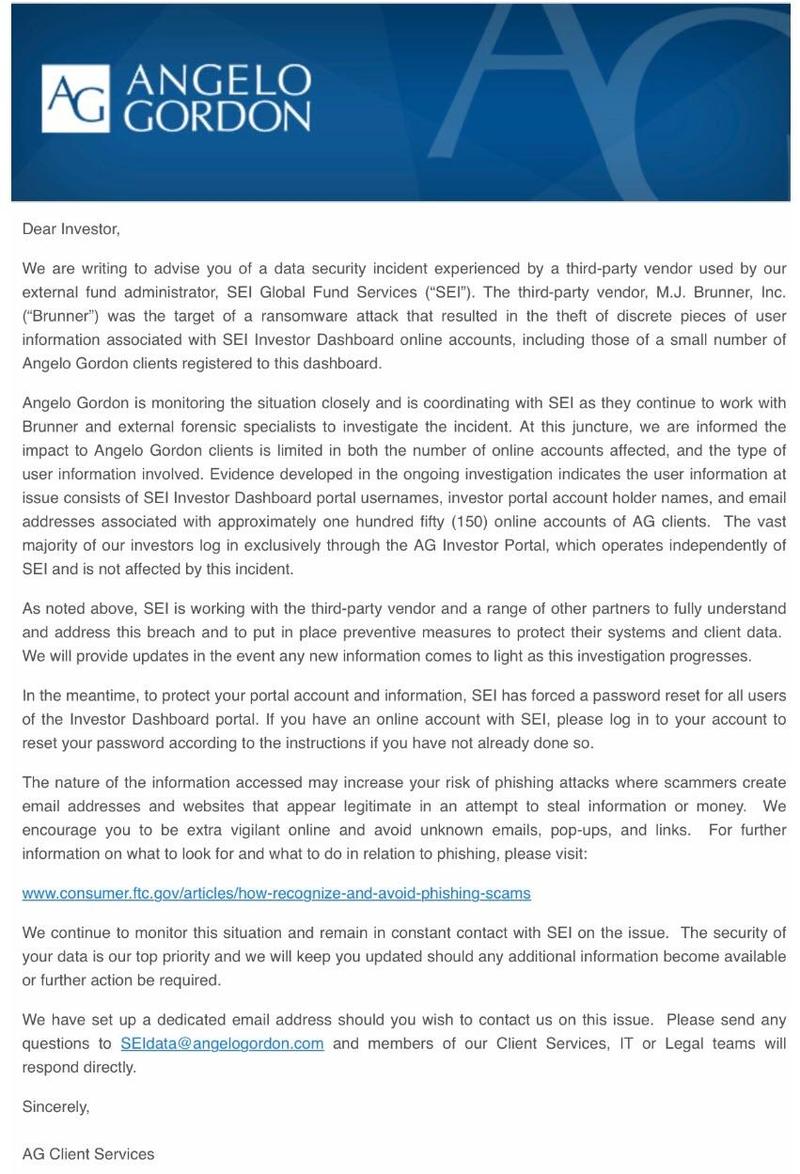
The hacked “third-party vendor” in question is M.J. Brunner, a Pittsburgh- and Atlanta-based service provider that developed and supports SEI’s investment dashboard and online enrollment portal, was the target of a ransomware attack that resulted in what the letter described as theft of “discrete pieces of user information associated with SEI Investor Dashboard online accounts.”
And since countless other hedge funds also use the same fund administrator, Dow Jones today reports that the hack attack also exposed secret information belonging to clients of such iconic funds as Graham Capital, Fortress, Centerbridge and even PIMCO, demonstrating again that all hackers need is to isolate the weakest link in any security chain and all personal information becomes immediately exposed for the world to see.
In this particular case, the unidentified hackers took files from Brunner that contained user names and emails – and in some cases names, physical addresses and phone numbers – associated with the dashboard.
The full data dump from the Ransomware attack, which has over 570GB in data, has been published online by a group called RagnarLocker at mazenews.top, a site historically linked with phishing attempts. The compromised data includes everything from usernames and passwords, but more importantly, SQL files that include live client data, including positions, trades, and P&L statements.
The Oaks, Pa.-based SEI is a leading fund administrator that does business with a broad swath of hedge funds and private-equity funds. As of June 30, SEI had $693 billion in client assets under administration and managed or advised on additional assets.
According to a Dow Jones report, Brunner was asked to pay a ransom but declined, prompting the hackers to post company data obtained from the May exfiltration online in July. Investors in funds like those SEI counts as clients include pension funds, endowments and wealthy individuals and families. Brunner told SEI about the attack in late May, but weeks passed before SEI knew its clients’ information had been breached, people familiar with the matter said.
Curiously, there was also no mention of the devastating ransomware attack during SEI’s Wednesday earnings call; we hope the management team issues an 8K addressing this minor “oversight.” A spokeswoman for SEI told Dow Jones that the company’s network wasn’t compromised and the attack wasn’t predicated on a vulnerability within its network.
“We take our clients’ security very seriously, and we are working with Brunner, the FBI and our impacted clients to understand the extent to which SEI’s or our clients’ data has been exposed,” she said.
A Brunner spokesman said in a statement its IT staff “detected, and interrupted, a security incident involving some of our corporate systems by an unauthorized actor. We immediately notified the FBI and will continue to work with them through their investigation.”
Meanwhile, in its letter, Angelo Gordon said it was monitoring the situation closely and is coordinating with SEI as they continue to work with Brunner and external forensic specialists to investigate the incident.
At this juncture, we are informed the impact to Angelo Gordon clients is limited in both the number of online accounts affected, and the type of user information involved. Evidence developed in the ongoing investigation indicates the user information at issue consists of SEI Investor Dashboard portal usernames, investor portal account holder names, and email addresses associated with approximately one hundred fifty (150) online accounts of AG clients. The vast majority of our investors log in exclusively through the AG Investor Portal, which operates independently of SEI and is not affected by this incident.
In any case, we urge all clients of Angelo Gordon, as well as PIMCO, Fortress, and any other fund that uses SEI as a manager, to promptly change their log in credentials as their private data may well be in the open.
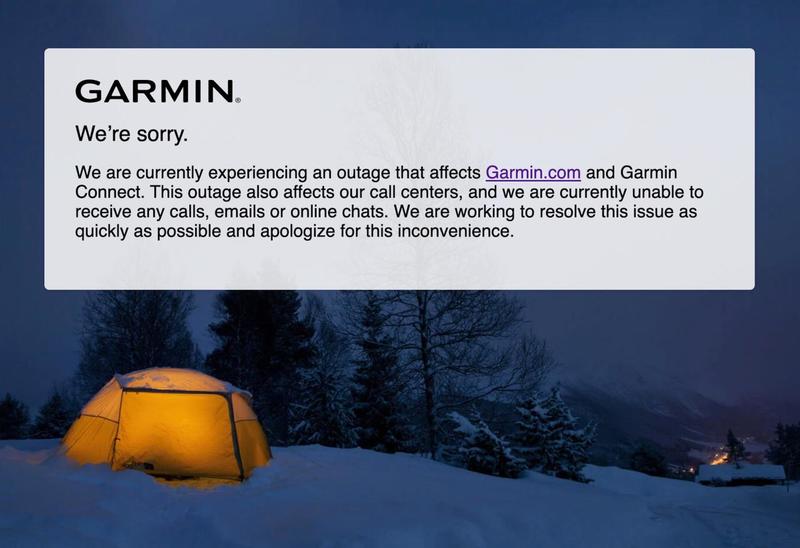
The attack is the latest in a string of ransomware incidents that have affected the financial-services sector through its far less secure suppliers. According to DJ, this past March financial-technology provider Finastra suffered an attack that forced it to temporarily take its systems offline. An attack on Finablr’s foreign-exchange business Travelex in late December shut down its website for weeks, which had a knock-on effect on banks that use its services. Garmin’s user data – which includes highly confidential personal health information – are currently locked out due to a suspected ransomware attack.
Officials from the National Security Agency have warned that vendors and service providers have emerged as popular targets, as successful attacks can yield access to large amounts of sensitive information for a web of clients, or even systems access.
Republished from ZeroHedge.com with permission









Sign up on lukeunfiltered.com or to check out our store on thebestpoliticalshirts.com.