WikiLeaks’ Vault 7 release of Central Intelligence Agency (CIA) documents yesterday opened eyes worldwide about an agency President John F. Kennedy once vowed to “splinter…into a thousand pieces and scatter it into the winds.”
Here’s a comprehensive list of ten things we didn’t know about the CIA before yesterday’s leak.
1. The CIA has an illegal domestic spying apparatus similar to the NSA
Perhaps one of the most revealing things that we learned yesterday is that the CIA’s domestic surveillance capabilities rival and may well surpass those of the National Security Agency (NSA).
While both agencies were required under the Obama administration to report vulnerabilities found in hardware and software to manufacturers, each failed to do so – endangering national security and personal privacy by weakening encryption and in the NSA’s case installing backdoors in consumer electronic devices. Obama’s loophole of the disclosure was that the agencies didn’t have to disclose exploits found if it helped them.
In 2014, Michael Daniel, a former National Security Council cybersecurity coordinator and special adviser to the president on cybersecurity issues, told WIRED that the government doesn’t stockpile large numbers of zero days for use.
“There’s often this image that the government has spent a lot of time and effort to discover vulnerabilities that we’ve stockpiled in huge numbers … The reality is just not nearly as stark or as interesting as that,” he said.
The agencies did just that hoarding zero-day vulnerabilities, exposing systems to other malicious hackers – whether they are foreign governments or criminals, violating the Consumer Protection Act.
In doing so, both agencies also violated the Fourth Amendment which protects against unauthorized search or seizure. The CIA admitted in 2014 to the Guardian that it was obliged to follow federal surveillance laws, laws that we now know both the NSA and CIA have broken an unfathomable amount of times.
The NSA itself violated surveillance restrictions thousands of times so the question must be proposed how many times did the CIA violate those surveillance restrictions?
How can Americans trust the CIA or the NSA, when the two agencies made us less safe by breaking the law and endangering private information such as bank account numbers and credit card numbers, by keeping security holes open in the devices of millions of Americans, just so they could exploit them. As security expert Bruce Schneier said back in 2013, “It’s sheer folly to believe that only the NSA can exploit the vulnerabilities they create.”
2. The CIA has a secret base in Germany
The CIA has a secret U.S. hacking base at the consulate in Frankfurt, Germany that it would disguise as State Department employees. The CIA even instructed its employees at the base how to avoid German security and gave them a cover story. This base is now under investigation by German authorities.
CIA hackers operating out of the Frankfurt consulate ( “Center for Cyber Intelligence Europe” or CCIE) are given diplomatic (“black”) passports and State Department cover. The instructions for incoming CIA hackers make Germany’s counter-intelligence efforts appear inconsequential: “Breeze through German Customs because you have your cover-for-action story down pat, and all they did was stamp your passport”
Your Cover Story (for this trip)
Q: Why are you here?
A: Supporting technical consultations at the Consulate.
3. The CIA has a cyber group dedicated to forging other countries digital fingerprints in false-flag attacks
The CIA has a secret espionage group called UMBRAGE that is dedicated to forging malware signatures of other countries including Russia.
The group collects and maintains a substantial library of attack techniques ‘stolen’ from malware produced in other countries.
With UMBRAGE and related projects, the CIA cannot only increase its total number of attack types, but also misdirect attribution by leaving behind the “fingerprints” of the groups that the attack techniques were stolen from – allowing them to create cyber false-flag attacks in which they can attack targets in the U.S. and blame another country for the resulting damages.
4. The CIA can spy on you through your smart TV and tap into the microphone
What was absent from Edward Snowden’s leaks was evidence of the ability for the NSA to spy on you through your smart TV. The CIA has found a way to do so through a program it called “Weeping Angel.”
5. The CIA can spy on you through any tablet or phone
While the NSA displayed similar capabilities to breach a phone or tablet’s security and hijack its camera or intercept text messages, the CIA proved it could do more.
Through it’s Mobile Devices Branch (MDB) they can exploit Android and Apple phones and tablets to do numerous attacks to remotely hack and control popular smart phones. Infected phones then can be instructed to send the CIA the user’s geo-location, audio and text communications, as well as covertly activate the phone’s camera and microphone.
6. The CIA can transcribe your Skype conversations
Kim Dotcom and 0hour explain how this is done in the following tweets.
https://twitter.com/0hour__1/status/839538363640266763
7. The CIA has exploits for every major Anti-virus software provider and major personal computer software programs, including Microsoft Word, VLC, and all operating systems
Wikileaks notes that a program called Fine Dining provides 24 decoy applications for CIA spies to use. To witnesses, the spy appears to be running a program showing videos (e.g VLC), presenting slides (Prezi), playing a computer game (Breakout2, 2048) or even running a fake virus scanner (Kaspersky, McAfee, Sophos). But while the decoy application is on the screen, the underlying system is automatically infected and ransacked. This would allow CIA agents to pose as testing a company’s security and appear as if they were really an IT tech, when in reality they were pillaging data. Wikileaks also revealed that the CIA has exploits for Windows, Linux, and Mac OSX based systems as well as general software exploits for various applications on all three OS versions.
8. The CIA can hack vehicle control modules including cars, trains, and planes
Ex-FBI Head of Los Angelas Ted L. Gunderson said that the way that the elite get rid of people is through trains, cars and plane accidents. While the capabilities of hacking vehicles may not be something new, the evidence that the CIA has this capability warrants looking back at several suspicious incidents in the past few decades which raised flags as being possible assassinations rather than simple misfortunate accidents. Yesterday We Are Change reported on journalist Michael Hastings’ suspicious death, but many others that raise suspicion include John F. Kennedy Jr’s death and Senator Paul Wellstone – both powerful political dissenters that died in strange plane crashes.
https://www.youtube.com/watch?v=xMQifcCb2M8
9. The CIA has an air gap virus that can infect systems even if not connected to the internet
Air gapping is a technique this reporter personally learned about in 2015 when a whistleblower personally came to me with what sounded like insane information.
Hint all new computer systems and cell phones hardware can be hacked via its radio signal Its called Air Gapping.#Security What Security?
— AKilluminati (AK)?? (@An0nKn0wledge) July 27, 2015
What is air gapping? Well it’s hacking a computer that isn’t connected to the internet.
Using the GSM network, electromagnetic waves and a basic low-end mobile phone through intercepting RF radio signals, researchers in Israel found they could extract data from computers, and Wired has now reported. Two weeks ago Wired reported that a drone has that type of capability, simply by watching a PC’s blinking led light – an incredible finding. Add that together with the CIA being able to implant malware and you have a dangerous weapon in the CIA’s hacking arsenal.
The CIA’s “Hammer Drill” infects software distributed on CD/DVDs, they have infectors for removable media such as USBs, and systems to hide data in images or in covert disk areas ( “Brutal Kangaroo”).
10. The CIA has a Meme Warfare Center. The meme war – is real.
The CIA actually has a meme warfare center which it uses to spread memes – giving cause for concern to anyone worried about government propaganda. Meme warfare is real, and the CIA has apparently been using it to spread disinformation. This is Operation Mockingbird in the 21st Century.
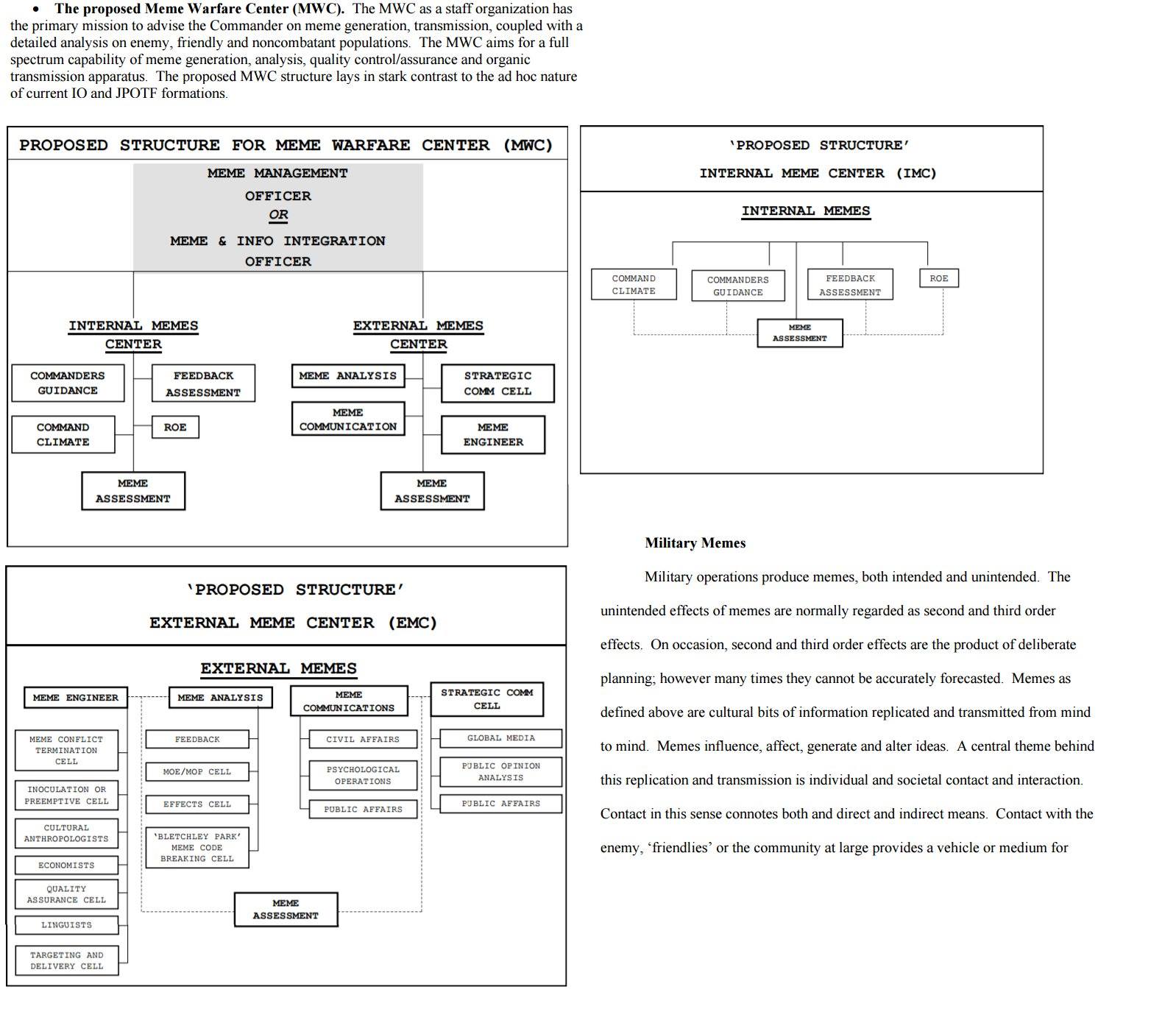
The CIA is not a friend to the people of the U.S., historically serving only the Wall Street and military-industrial complex elite. The CIA has been caught before spying domestically in the 1960’s – 70’s, including spying on journalists under Operation CELOTEX I-II and others in 702 documents called the “family jewels,” that catalog the agency’s domestic wiretapping operations, failed assassination plots, mind-control experiments and more during the early years of the CIA.
The CIA is the deep state, and it is dangerous.
What do you think of this list did we miss something that we should have covered? Let us know in the comment section below!










Sign up on lukeunfiltered.com or to check out our store on thebestpoliticalshirts.com.