
Written with the assistance of Rory Byrne Co-Founder of @securityfirst, “building tools for the security of human rights defenders.”
[ Today’s ] journalists and activists are increasingly under threat from digital and physical surveillance.
Basic training;
Here are some very basic steps on how to protect yourself when you feel like you might be being tailed, tracked, or followed. Note this article is not meant to trigger or inspire any occurrence of targeted individualism but only as a brief guide line for those who wish to learn how to identify and neutralize physical surveillance. Let’s be clear: if the professionals are following you, you probably won’t know it. Well trained spies use a host of tricks that make sure you’ll never know you’re being followed.
What is Surveillance?
Surveillance is the monitoring of people’s behavior, activities, or other patterns for the purpose of harming, influencing, managing, directing, or protecting them.
Why might people be interested in keeping you under physical surveillance?
- Break-in/ theft of sensitive materials
- Arrest
- Monitor who is coming and going from the office
- Intimidation
- Physical attack on staff
Who might be interested in keeping you under surveillance?
- Authorities of the country in which you conduct your journalist or activism work
- External security agencies of other countries in the region
- Criminals?—?including kidnappers and stalkers
- Terrorists
- Private contractors
- Embassy officials of “friendly” countries
- Local people in your community
- Individuals (may be disgruntled with your organisation)
What techniques are available to carry out surveillance?
• Digital surveillance (monitoring of digital communications, mobile phones etc.)
• Human surveillance (on foot, in a vehicle)
• Technical surveillance (bugs, listening devices, video cameras, number plate readers etc.)
How to Identify if Your Office is Under Surveillance
Surveillance generally requires that the adversary is able to observe the activities of its targets. This means there are a limited number of physical sites they can use for surveillance. The best thing to do when looking for surveillance is to try to think like an adversary?—?what might you do is you were trying to monitor your office? From where might you carry out such surveillance?
• Take a baseline
It is important to gain an understanding of what “normal” conditions look like. (For example, where cars normally park or people normally stand).
• Identify and record
From this, try to identify and record any unusual activities. (For example, people in locations where they shouldn’t be or aren’t normally).
• Filter out coincidence
Filter out the chances that something could be a coincidence by concentrating on unusual activities and applying common sense filters (e.g. if someone is standing in a place where people don?t normally stand pay more attention to them. Do they look like they are from the area? Are they paying an unusual amount of attention to your activities?) Look for 3 signs that something is out of the ordinary or 3 repeat sightings.
• Notify others
It is important to notify others of any suspicions and to keep a log of them. This allows the monitoring of patterns which otherwise might not emerge. For example, if you notice someone suspicious and then a colleague notices something else suspicious on a separate occasion but this information is not shared, then a valuable opportunity to confirm a security threat is missed.
• Trust your senses
Trust your senses – there may be clues of a potential arrest or violent attack. Often, journalists and activists report that there were warning signs prior to an attack, but they chose to ignore the warning signs or dismissed it as paranoia.
What To Do If Your Office Is Under Surveillance
- Consider the risks
Confrontation with suspicious people should be done with caution, before doing so, consider the risks. For example, what might that person be doing? What is the past history of threats against your organisation or yourself? Is it likely that they will attack you immediately if you confront them or is it more likely that they will just leave and send someone else? If you confront someone they are likely to be replaced by another (unknown) agent, and you then lose the benefit of being able to monitor the surveillance being carried out against you. - Increase protection
Increase your office protection by reducing the ability of an adversary to conduct surveillance. For example by putting up screening near your building, using CCTV and/or guards, closing blinds, locking gates, selecting sites which are not easily overlooked, strict access controls to your building etc. - Continue monitoring
Continue to monitor the general security environment and increase your observation of threats during periods of higher tension ? e.g. protests, elections, sensitive national holidays etc.
Countering Physical Surveillance
Physical surveillance continues to be a significant danger to those working on journalism and human rights. Other than a human source, it is the only way to build detail on what is occurring things like meetings. It is obviously important to know how to identify if you, your colleagues, or partners are under surveillance.
Counter-surveillance is the process of detecting and mitigating hostile surveillance.
Tells that might give away someone who is conducting surveillance on foot include:
— Readjusting personal equipment
— Touching earpiece
— Visibly talking into their microphones
— Glazed eyes
— Unusual behavior or demeanor
— Trying to avoid the target’s gaze
— Looking around corners/through windows
— Mirroring behaviour
— Stopping in unusual places
Identifying Teams
If you identify one potential surveillance member, you can use that knowledge to identify others. Members of a surveillance team can cross-contaminate other members:
• By speaking directly to them
• By looking in their direction
• By using hand signals
• By appearing or dressing in a similar manner
What can you do to spot them?
The most important thing to remember when conducting counter-surveillance is that you need to be discreet as you do not want any potential surveillance teams to know that you are looking for them. This would raise suspicions further about what you intended to do. The primary aim is to ascertain whether or not you are being followed, not to lose them.
Remember, if you discover you are in fact under surveillance, you have three options:
• Change your plans: This is the safest and recommended option ? it will allow you to keep your original plans to yourself and reassure whoever had you under surveillance that you aren’t up to anything suspicious or worthy of surveillance.
• Lose the surveillance covertly: This is losing the surveillance team without them knowing you were aware of them by making it look accidental. This should be used if you absolutely must keep your plans and you feel it is safe to do so.
• Lose the surveillance overtly: This trying to identify or lose the surveillance team in a way that makes them aware of what you are trying to do. This is a risky tactic because it confirms to the team that you are indenting to do something that you don’t want them to see and so are increases the likelihood of you being under continued surveillance. You should only conduct your counter-surveillance overtly if absolutely vital and it is not possible to do so covertly.
Five Rules of Counter-Surveillance
1. Trigger
This is the person who initially alerts the rest of the surveillance team when the target is on the move. The easiest person to find.
2. 10 to 2
The person carrying out the surveillance will try to stay out of a the 10 t0 2: the immediate eye line of the person they have put under surveillance
3. 3 times
This is the number of sightings of a surveillance team member you are aiming to achieve before you can confirm that you are under surveillance.
4. 3 sides of a square
This is the minimum number of turns you take to filter and reduce the possibility of seeing the same person by coincidence.
5. Breaking the box
This is the process of breaking out of the surveillance a team will try to keep you in. By breaking the box you increase the likelihood that they will make mistakes which you can observe and use to identify them.
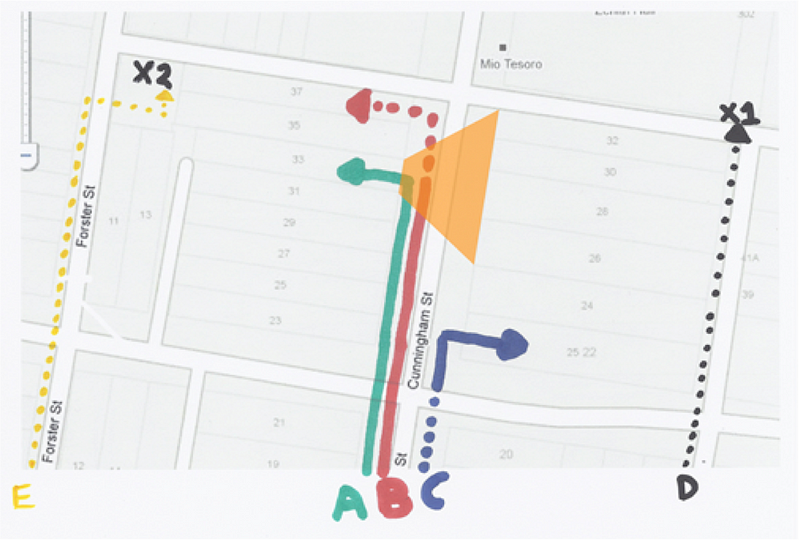
Tactics: Identify the Trigger
The trigger is the surveillance team member who initially alerts the rest of the surveillance team members (who will be spread out in a box around the target). They are unlikely to move when you leave your location as that may draw attention to themselves.
The easiest place for them to be located is in or outside your location. They will usually try to stay stationary. If the place you have entered has a number of exits then a number of team members may be spread around each as a trigger. Think about where you would be if you were on a surveillance team look for locations and situations where it would not be suspicious for a surveillance person to be hanging around.
Tactics: How to find the eyeball on foot
The eyeball refers to the member of the surveillance team who currently has you in their sights. Firstly?—?don’t look over your shoulder! Instead try to create situations to look observe all around you naturally?—?including behind you:

• Try using windows; either looking through them or in their reflection; or car mirrors;
• Hold open doors for other people to enter and let them overtake you;
• Cross a busy street and see who follows you;
• Stop to look at posters or bus timetables, use an ATM, or buy something from a street vendor.
Tactics: Create a force-past
A force-past is when you create a situation in which someone following you would have to go past you or expose their position. There are several easily created force-past points:
• Traffic crossing point
• Bus stop
• Taking an escalator
• Using a lift to go up (until all passengers have left), then go down and exiting via an underground car park
• Rapidly turning a corner then suddenly entering into a shop
• Go into a shop/pub/building through one entrance and then rapidly exit via another
• Corner hanging: turn a corner then rapidly stop
• Change your clothing to make it harder to identify you.
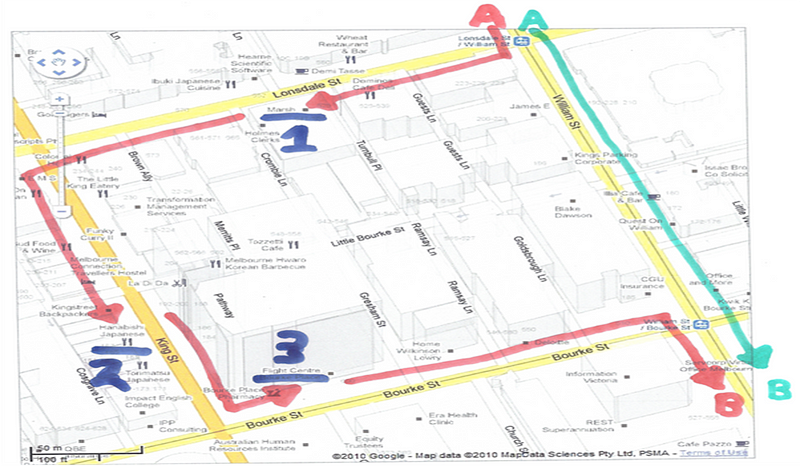
Three Sides to a Square
This is a technique used to identify several members of a team, create pressure on them and thin down their surveillance. It can be conducted alone or with a team.
It means taking a longer route than would logically make sense for someone going from point A to B.
Pick three or more reasons to be a) using such an unusual route and b) stopping along the way. These reasons should take the following things into account:
• It should be genuine and not suspicious, there should be a believable reason for the detour. Remember, this is because you do not want any possible surveillance to know that you are checking for surveillance
• It should force a surveillance team member to go into the location with you to establish what you are doing, who you are meeting, or check for any signs that you may have a counter-surveillance team with you
• It should be a position where you can:
– Observe what is occurring
– Observe the various exits/entrances
– Be out of the target’s 10 to 2 eye line
• You should be able to quickly get on the move again, so pay bills in advance, don’t get hot food, etc.
Additional Tactics:
– Get on a bus
It is difficult for surveillance teams to keep up if you suddenly get on a bus, going from on foot to mobile. This is particularly true because buses are slower than other vehicles so are difficult to follow by car too. Ensure you have change for the fare. Sit as far back in the bus as possible and if it?s left-hand drive, sit on the right side of the bus to be able to observe any vehicles which might over take the bus
If conducting overt anti-surveillance get on, get off at the next stop, and then rapidly get on the next bus. If you want to appear covert ? get on a bus with one number, then get off and get a bus with another number, to make it look like you might be lost.
– Get in a Taxi or on a Train or Ferry.
Trains are difficult to follow with multiple forms of surveillance because they are faster than other vehicles. When getting on the train, hang back and try to be the last person to get on. Stand at the end of the platform where the train driver stops and where you will have a good view. Try buying a ticket to a destination and observe?—?get off before that destination.
If conducting overt anti-surveillance, get off then rapidly change trains. If you want to appear covert get on a train with one destination, then get off and get a train with another destination, to make it look like you might be lost.
Taxis can be useful for local knowledge and the fact that in some countries they can use bus lanes which surveillance vehicles might not be able to use without drawing attention to themselves.

[Learn More Here]
Thank you !
Rory Byrne
Co-Founder of @_securityfirst, building tools for the security of human rights defenders. Helped setup and was Head of Security & Research.
Learn about Rory’s Umbrella Program Here.












Sign up on lukeunfiltered.com or to check out our store on thebestpoliticalshirts.com.