A faction within the Anonymous movement has claimed responsibility for hacking Freedom Hosting II, a hosting company for TOR based onion websites or the darknet.
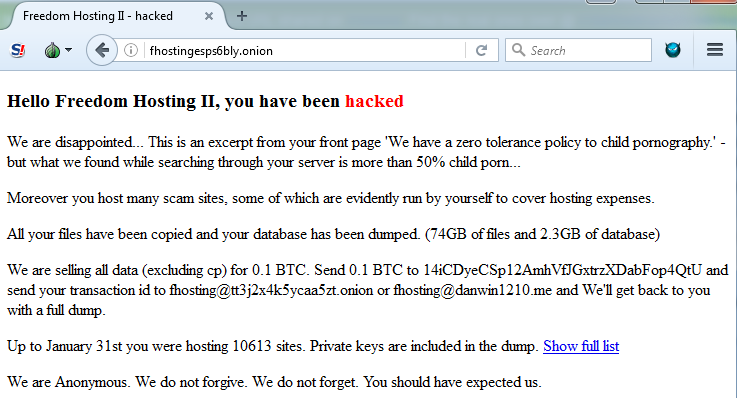
Visitors to various websites hosted on the darknet were met with the message, “Hello, Freedom Hosting II, you have been hacked.”
The full statement read:
Hello Freedom Hosting II, you have been hacked
We are disappointed… This is an excerpt from your front page ‘We have a zero tolerance policy to child pornography.’?—?but what we found while searching through your server is more than 50% child porn…
Moreover you host many scam sites, some of which are evidently run by yourself to cover hosting expenses.
All your files have been copied and your database has been dumped. (74GB of files and 2.3GB of database)
We are selling all data (excluding cp) for 0.1 BTC. Send 0.1 BTC to 14iCDyeCSp12AmhVfJGxtrzXDabFop4QtU and send your transaction id to [email protected] or [email protected] and We’ll get back to you with a full dump.
Up to January 31st you were hosting 10613 sites. Private keys are included in the dump. Show full list
We are Anonymous. We do not forgive. We do not forget. You should have expected us.
The hackers claimed that child pornography made up more than half of the data that was hosted on the servers.
This is not surprising considering the fact that the original Freedom Hosting hosted as many as half of the child porn sites on the darknet.
The service was compromised by law enforcement in August 2013, and its owner Eric Eoin Marques was arrested. The FBI used a firefox tor exploit to exploit javascript, and then trace and capture several pedophiles.
All of the sites hosted by Freedom Hosting—some with no connection to child porn—began showing an error message with hidden code embedded in the page. Security researchers dissected the code and found it exploited a vulnerability in Firefox to identify users of the Tor Browser Bundle, reporting back to a home server in Northern Virginia.
The latest attack is not suspected to have been done by the FBI, but by online vigilantes who have deemed themselves “pedophile hunters.”
The hackers have since dumped the data, and it includes the email addresses of nearly 381,000 users. At least 21 percent of them are already included on haveibeenpwned.com, a website that tracks user data leaks.
New sensitive breach: Freedom Hosting II had 381k email addresses exposed. 21% were already in @haveibeenpwned https://t.co/LGaAnj1hUA
— Have I been pwned? (@haveibeenpwned) February 5, 2017
Troy Hunt, a security researcher, noted that there were thousands of .gov email addresses. Although as he said, “how many are real and what purposes they are being used for is another issue,” as not everything hosted on Freedom Hosting II was child pornography. However, he added, “much of the data is highly explicit,” with half of the sites in the dump containing illicit sexual pictures of children. An ongoing analysis of the leak can be found on Medium, where Chris Monteiro is looking into the data.
Thousands of .gov emails. How many are real and what purposes they were being used for is another issue. https://t.co/31fQoWG4qj
— Troy Hunt (@troyhunt) February 5, 2017
In the meantime, another hacker “eTrappin,” I personally know is working on a tool to trace these pedophile websites called “tortrace.” He is welcoming all help coding the tool.
New Tool Under Development To Target Underground Pedo Rings TorTrace If U Can Help Code Contact @eTrappin:https://t.co/dxOp5fO7hw
— AKilluminati (AK)?? (@An0nKn0wledge) February 3, 2017
This is a huge blow to the pedophile darknet, which is mostly hosted by Freedom Hosting. Anonymous has previously gone after the darknet with an operation a few years back called “Operation Darknet.”










Sign up on lukeunfiltered.com or to check out our store on thebestpoliticalshirts.com.