Internet privacy is becoming more and more important to understand as companies and governments are now collecting our information daily via the Internet.
Throughout the next few articles, I’ll be highlighting a few of the more practical ways we can begin to take back our Internet privacy and improve our online experience.
 1. Tor: Protecting Your Online Privacy
1. Tor: Protecting Your Online Privacy
Whether you’re an activist, journalist, casual Internet researcher, business professional or just someone who wants a bit more privacy, Tor is about as good as it gets for internet security.
Tor, which stands for The Onion Router, is a “network of virtual tunnels”, which protects you from a specific type of network surveillance called “traffic analysis”.
Tor has the unique ability to reroute your Internet traffic through a minimum of 3 different IP addresses for the purpose of masking your current location and Internet activity.
Tor’s technology was originally developed by the U.S. Naval Research Laboratory as an effective way for protecting government communications. As civilians, we now have this technology available to us.
Each computer involved in the Tor network can only see one hop in the circuit, so your final destination won’t know where you’re searching from.
Ex: 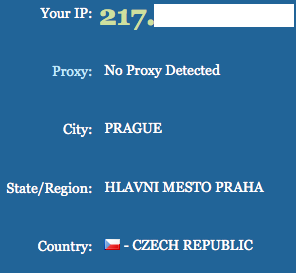
In the screenshot above, although I’m located in Massachusetts, when I look up my IP address using Tor, it shows that the “node” that requested this data was from a computer located in Prague, Czech Republic.
In addition to it’s practicality, Tor is free and open source. However, it appears that nothing these days is completely out of the grasps of the NSA so do your due diligence.
Individuals currently use Tor to:
1) Prevent websites from tracking them
2) Access websites and services which have been blocked by their Internet providers
3) Publish websites anonymously
4) Exchange confidential information with other individuals
For more information on the Tor Project, you can visit https://www.torproject.org/.
Check back soon for Internet Privacy Part 2:
Blocking Ad Trackers With Ghostery
Tyler Ebeling
We Are Change









Sign up on lukeunfiltered.com or to check out our store on thebestpoliticalshirts.com.